It was late in the afternoon when my phone buzzed with a new SMS. The message caught my eye, not because I believed it, but because unraveling scams like this has always intrigued me. Little did I know, this text would lead me down a rabbit hole of discovery, shedding light on how modern SMiShing (SMS phishing) schemes operate.
Here’s how it all unfolded.
The text was straightforward, appearing to come from CIBC, a major Canadian bank. The message requested I verify my account by clicking a link. Accompanying it was a crisp graphic, professional enough to appear legitimate to an unsuspecting recipient. But my instincts told me otherwise—major banks don’t request sensitive actions via SMS.
Still, curiosity had the better of me, and I decided to investigate.
Tracking the Origin
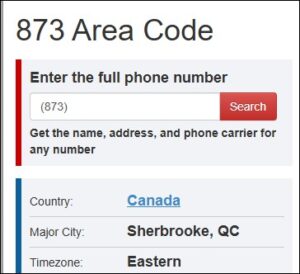
The phone number that sent the message bore the 873 area code, originating from Quebec, specifically Sherbrooke. That was the first anomaly—banks typically don’t use random regional numbers for official communications.
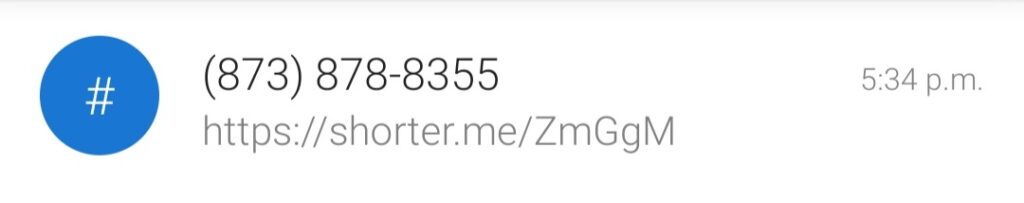
The link provided was a shortened URL, a common tactic used by scammers to obscure the actual destination. Shortened links have legitimate uses: they save space, look clean, and can even offer analytics. But in the wrong hands, they become tools for deception.
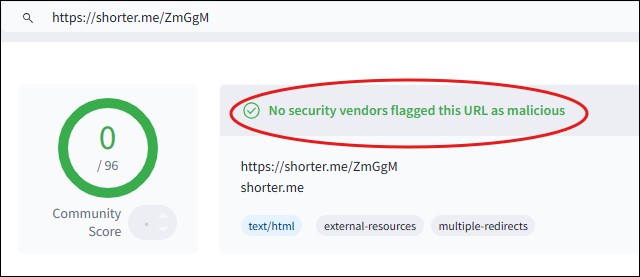
Instead of clicking the link—a definite no-go—I copied it into VirusTotal, a trusted service for analyzing suspicious URLs. The results came back clean, which is often how these scams bypass basic detection methods.

But I wasn’t convinced. The details revealed the final destination: a domain called verifycibclogin[.]com.
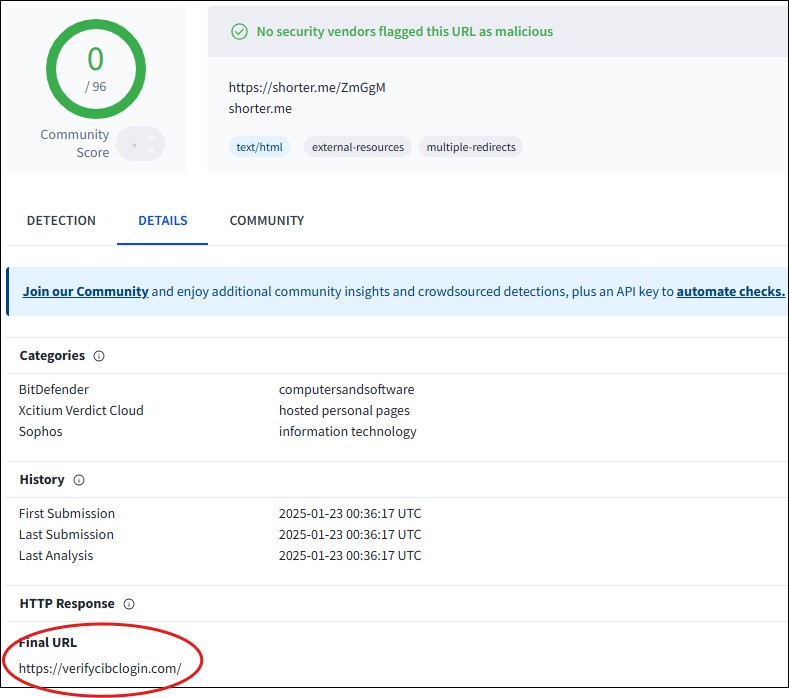
Would a reputable bank use such an oddly phrased domain? Unlikely.
Digging Deeper into the Domain
A quick domain search revealed that the owner had hidden their identity—a red flag. Legitimate organizations rarely mask their domain registration details.
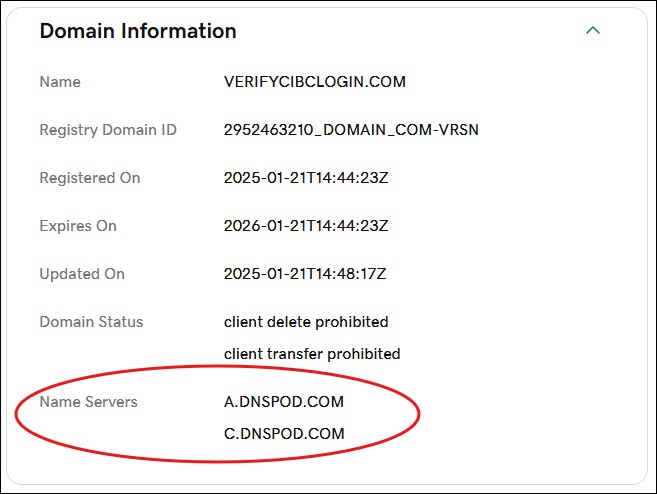
So, I decided to look deeper into where these DNS servers resided. First, I pinged this domain to identify the IP address.
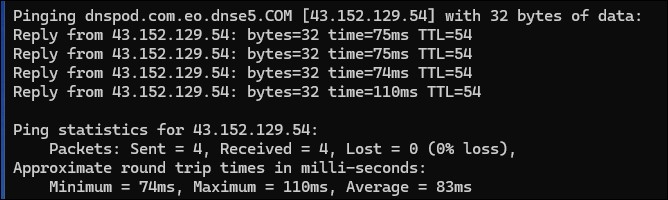
Next, I pinged the domain to uncover its IP address and traced it via ARIN.net, a registry for IP information. The results? The DNS provider was based in Singapore, a financial hub for sure, but not a logical location for a Canadian bank’s operations. The trail was beginning to reveal its true nature.
Lastly, I wanted to dig a little deeper into the strange domain a little more, so I use the same steps that I used to discover the IP address of the DNS server. By pinging the verifycibclogin[.]com domain I received the following:
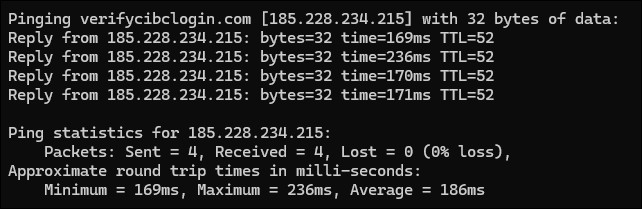
And with this information I once again checked ARIN.net to find the final stop on the journey.
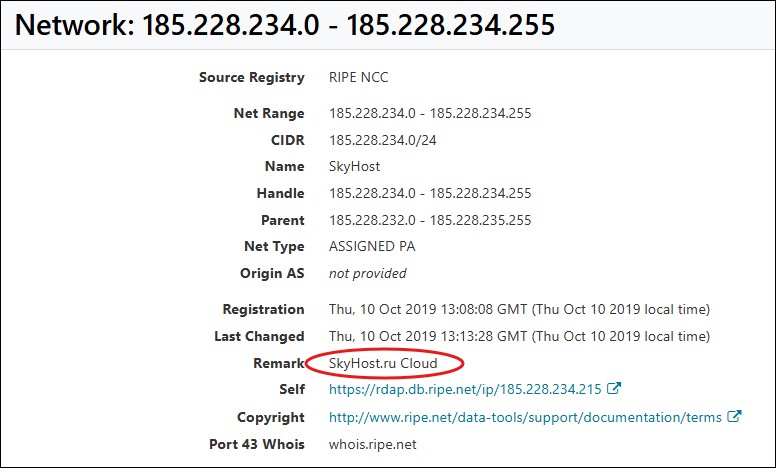
The domain itself was hosted by a Russian cloud provider. The trail was beginning to reveal its true nature.
The Bigger Picture
In just a few steps, I unraveled a complex web of deception. A text message originating from Quebec led to a DNS provider in Singapore and finally to a domain hosted in Russia. Each layer was designed to mislead, creating just enough plausibility to lure in victims.
This SMiShing attempt highlights the sophistication of modern cyber threats. The use of professional visuals, plausible messaging, and obscured links shows how scammers rely on trust and human curiosity to exploit their targets.
Key Takeaways for Protecting Yourself:
- Never click on links in unsolicited messages, especially if they ask for sensitive information.
- Use tools like VirusTotal to analyze suspicious URLs without risking a direct visit.
- Look for inconsistencies in domain names, area codes, and geographic locations.
- Report suspicious messages to your bank or local authorities to help protect others.
Stay vigilant—because in the age of digital communication, even the most convincing message can be a carefully crafted trap.


